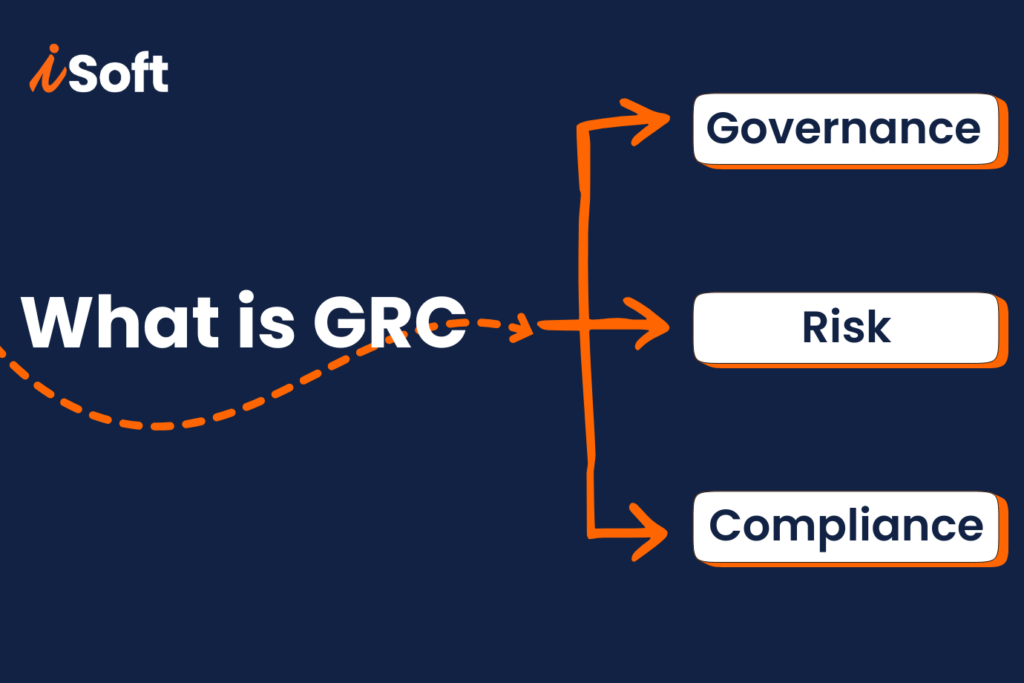
What is GRC? A Complete Guide to Governance, Risk, and Compliance
The digital threats in the technology world are getting sophisticated by the day, and I have seen companies realize that they have no other option but to have a proper consensus on the procedures and processes with which they deal with such threats. As a professional thoroughly involved in the industry, I can tell you […]
What is GRC? A Complete Guide to Governance, Risk, and Compliance Read More »