Comprehensive Data Loss Prevention Services
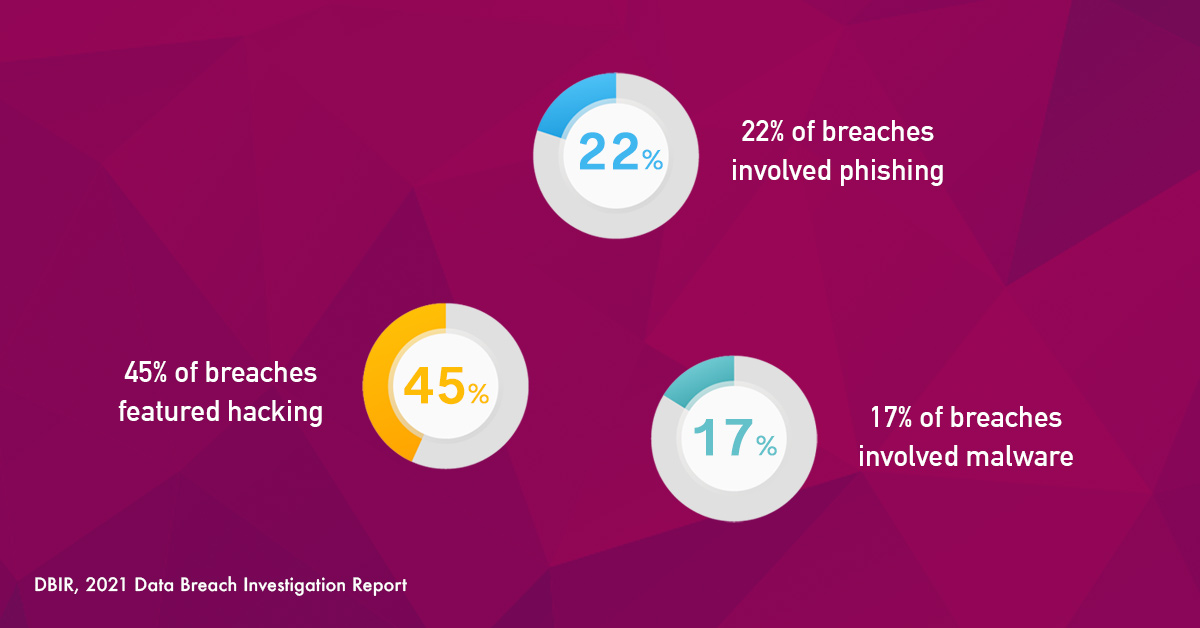
In an era where data breaches and cyber threats are increasingly sophisticated, organizations must prioritize robust data protection services to safeguard their sensitive information. Effective data loss prevention (DLP) is crucial for protecting against unauthorized access, accidental data leaks, and cyber attacks. Our comprehensive data protection services are designed to address these challenges, providing a secure environment for your organization's critical data.

What are Data Protection Services?
Data protection services encompass a range of strategies and tools aimed at securing data throughout its lifecycle. These services ensure data loss prevention from unauthorized access, corruption, or loss, whether it is in use, in motion, or at rest. Our data protection services start with classifying and continuously monitoring your data. This allows us to identify sensitive information and ensure it is handled appropriately according to its level of sensitivity. We implement and enforce strict data protection policies to prevent unauthorized access and data leaks. These policies cover data encryption, access controls, and secure data handling practices.
Our data loss prevention services include real-time alerts and detailed reporting on any suspicious activity or potential security incidents. This enables quick response and mitigation to prevent data loss. Data protection services at iSoft monitors user activities that helps in detecting unusual or unauthorized actions that may indicate a potential security threat, allowing for timely intervention.
In the event of a data breach, our incident response team is ready to act swiftly to mitigate damage, conduct thorough investigations, and implement measures to ensure data loss prevention in future.
Data Loss Prevention (DLP) through Dark Web:
In the depths of the internet lies the dark web, a hidden realm where cybercriminals operate in anonymity, trading stolen data and plotting cyber attacks. As businesses and individuals alike navigate the digital landscape, the threat of data breaches and leaks looms large. Dark Web Monitoring and Data Loss Prevention have emerged as essential tools in the fight against cybercrime. At iSoft, we offer comprehensive solutions to monitor the dark web and prevent unauthorized data leaks.
The dark web is a hidden part of the internet that is not indexed by traditional search engines. What makes Dark Web Monitoring difficult is its operations on encrypted networks, allowing users to remain anonymous. Cybercriminals exploit the dark web to buy and sell stolen data, such as login credentials, financial information, and personal details. Monitoring the dark web is crucial for businesses to identify if their sensitive data has been compromised and is being traded illegally. The Data Leak Prevention solutions provided by iSoft have been instrumental in protecting our client’s sensitive information.
iSoft diligently monitors the dark web to safeguard both public and private sector organisations. Our service, Dark Web ID scan, leverages a combination of human and artificial intelligence to continuously monitor botnets, bulletin boards, peer-to-peer and private networks, and various other black market sites to ensure Data Leak Prevention.
Operating 24/7, 365 days a year, we identify stolen credentials and other personally identifiable information, providing comprehensive protection against cyber threats and potential data breaches. Dark Web Monitoring allows us to detect potential threats early, before they escalate into major security incidents. By monitoring the dark web, we can proactively identify vulnerabilities in your security posture and take necessary action towards Data Leak Prevention. We protect your sensitive data from falling into the wrong hands through our tailored Data Leak Prevention solutions.
Where Do We Find Data?
- Dark web chatroom: Compromised data discovered in a hidden IRC.
- Hacking sites: Compromised data exposed on a hacked website or data dump site.
- Hidden theft forum: Compromised data published within a hacking forum or community.
- P2P file leak: Compromised data leaked from a peer-to-peer file-sharing program or network.
- Social media post: Compromised data posted on a social media platform.