Home » Vulnerability Scan
Vulnerability Assessment & Management
Vulnerability Assessment is a proactive process of identifying, quantifying, and prioritizing vulnerabilities in an organization's IT infrastructure. It involves using a combination of automated tools and manual techniques to scan systems, networks, and applications for weaknesses that could be exploited by cyber attackers. The primary goal of Vulnerability Assessment is to provide organizations with actionable insights to remediate vulnerabilities and reduce the risk of security incidents. iSoft helps SMBs meet industry-specific compliance requirements by conducting regular vulnerability assessments. We specialize in providing Vulnerability Assessment services tailored for the unique needs and challenges faced by SMBs.

At iSoft, we offer comprehensive Vulnerability Assessment and Penetration Testing (VAPT)to help organizations fortify their cybersecurity defenses and protect against evolving threats.iSoft cyber team involves setting up one or more dedicated security vulnerability scanners on your computer network. The scanner is designed to check every device on your network — including servers, desktop computers, mobile devices, printers, network phones, etc. — and look for known vulnerabilities. We can also use our external scanners to perform the same vulnerability scan on your firewall.
Vulnerability Assessment and Penetration Testing (VAPT)go hand in hand at iSoft. We program it to run automatically at a specific time interval and set up a schedule for routine network adjustments based on the results of the scan data. Moreover, the frequency of scans and scheduled security sessions will depend on your specific situation. We collaborate with organizations to define the scope of the VAPT testing, including systems, networks, and applications to be tested. Automated scans are conducted using industry-leading tools to identify known vulnerabilities and misconfigurations.
Vulnerability assessment is categorized based on their severity and potential impact. Vulnerabilities are exploited in a controlled manner to demonstrate their impact and potential risks. The results of the VAPT testing are analyzed to provide insights into potential attack scenarios and the effectiveness of existing security measures. A detailed report including summary, severity ratings, proof-of-concept demonstrations, and actionable recommendations for remediation, is provided from both the Vulnerability Assessment and Penetration Testing (VAPT).
Each VAPT testing is tailored to the specific needs and infrastructure of the organization, ensuring a targeted and effective approach.
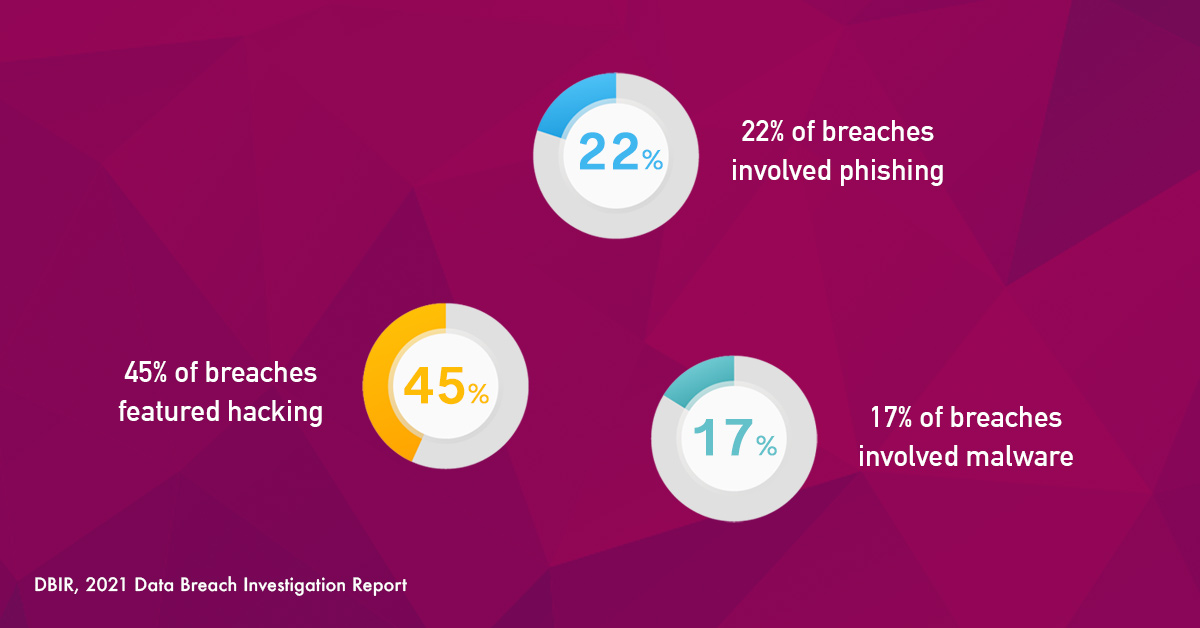
If You Are An SMB, It Can Happen To You!
- 57% of data breaches that SMBs suffered involved external threat actors.
- $2.98 millionis the average cost of a data breach for SMBs with <500 worldwide
- Only 47% of SMBs are identifying breaches within days.
- 43% of SMBs do not have any cybersecurity defence plans in place.
- 1 in 5 SMBs do not have any endpoint security protections.
Features
Comprehensive Scanning
Our external scanners check network firewalls and other “perimeter” defences, whereas our internal scanners check every device within the network. Both are centrally managed via a web-based portal.
Automation
Find vulnerabilities faster with easy-to-run vulnerability scans. It not only eliminates manual processes and repetitive steps while decreasing your exposure to vulnerabilities.
Customize Dashboards
Access scan results through our easy-to-use web-based portal, as high-level trend data and important info are displayed at the top.