ISO 27001 Consultancy Services
Trusted Cyber Security & Compliance Services







Why Choose iSoft for ISO 27001 Service?
Expert Knowledge
I possess over 15 years of experience in information security and as a result, I can produce a great amount of quality into each project.
Cutting-edge Tools
Our AI-designed compliance software-icon speed up certification stage with the technology of faster and more efficient.
Tailored Approach
We do not trust the principle of "one-size-fits-all". For us, the best strategies are those that are personalized to the unique needs of your business.
Proven Success
We are the outsiders who made it to the top 300 and have ISO 27001 to prove it from big name technology companies to startups all the way up to Fortune 500 giants.
What is ISO 27001
If there is no ISO 27001 conformance, the implications could include:
- The increased danger of data breaches resulting in the company’s immense expenses.
- The alienation of your clientele and a decrease in your brand’s market value.
- Issues resulting from inefficient operational processes.
- Vulnerability to cyber-attacks is heightened.
Regrettably, however, a constructive plan about ISO 27001 might lead to:
- Convinced decision-makers with reliable data on security issues.
- Security incident prevention savings.
- Client’s trust and loyalty reach sky-high levels.
- An elevated position in the market that could come at the expense of non-certified opponents.
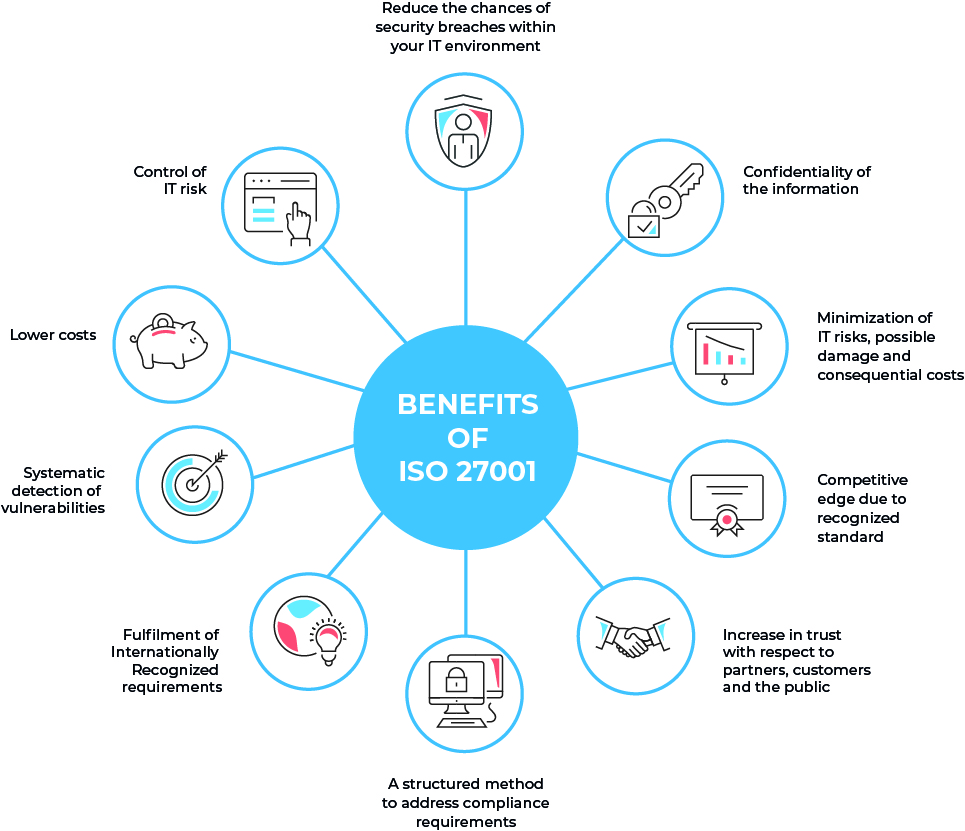
Key Benefits of ISO 27001 for Your Business
Enhanced Data Security
Protects sensitive business and customer data from breaches through structured, risk-based security management practices.
Regulatory Compliance
Helps meet global regulatory requirements and industry standards, reducing legal risks and non-compliance penalties.
Customer Trust & Reputation
Demonstrates your commitment to information security, building greater trust with clients, partners, and stakeholders.
Risk Management
Identifies, evaluates, and mitigates security risks before they impact operations, ensuring business continuity and resilience.
Operational Efficiency
Streamlines security processes, reduces redundancies, and ensures a systematic approach to managing information assets effectively.
Competitive Advantage & Growth
Gain a market edge by showing potential clients and stakeholders that you take compliance and risk management seriously.
Why ISO 27001 is Important?
Risk Management
We help you discover security flaws and take the necessary steps to correct them before they are exploited by criminals.
Legal Compliance
Abide by the regulations on data protection to escape being fined data breaches and the demands of privacy.
Clarity of Policy and Procedure
Our security protocols will guide you and thus you will be sure to make the right moves.
Customer Satisfaction
Clients can see if you are taking their data seriously, which in turn will make them loyal and will bring their trust to the highest level possible.
Competitor Advantage
We live in a time where data breaches are more frequent. ISO 27001 qualification will distinguish you from others.
Operational Efficiency
By getting rid of unnecessary operations, augmenting the value of the information technology department and thus achieving higher efficiency in work and better control of the budget, not opposite to this, downtime is getting minimized.
Is your business ISO 27001-compliant? Get a free assessment today!
Why Your Organization Needs ISO 27001
ISO 27001 is essential for organizations aiming to protect sensitive information and ensure long-term operational security. Implementing an ISO 27001-compliant Information Security Management System (ISMS) helps your business safeguard data, meet regulatory requirements, and reduce cybersecurity risks. It not only builds trust with clients and partners but also enhances your organization’s resilience against evolving threats and operational disruptions.
- Protects sensitive business and customer data from cyber threats.
- Demonstrates compliance with international information security standards.
- Builds trust and credibility with clients, partners, and stakeholders.
- Reduces the risk of data breaches, penalties, and operational downtime.
- Promotes a culture of continuous improvement in security practices.
Have Questions about ISO 27001? Find Answers Here
ISO 27001 is an internationally recognized standard that provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). It helps organizations protect their data systematically and cost-effectively through risk management, policies, and controls.
ISO 27001 is beneficial for professionals in cybersecurity, IT, auditing, and risk management, but it’s also highly valuable for business owners, compliance officers, and even startup founders. If your work involves handling, storing, or managing sensitive or customer data, understanding ISO 27001 is a smart move.
Not at all. While tech and IT companies often adopt it first, ISO 27001 is industry-agnostic. It’s equally applicable to healthcare providers, financial institutions, educational organizations, legal firms, and any business dealing with confidential information that needs protection against internal and external threats.
For individuals, ISO 27001 training and certification can take a few days to weeks, depending on the level (foundation, lead implementer, auditor). For organizations, certification usually takes between 3–6 months or more, depending on company size, current security maturity, and resource availability.
An ISMS includes risk assessments, information security policies, asset management, access control, incident response, business continuity planning, internal audits, and continuous improvement. These components work together to protect sensitive information and ensure your business can respond to evolving threats effectively.
ISO 27001 provides a structured approach to managing and protecting sensitive information. It helps your company prevent data breaches, comply with legal and regulatory requirements, and build trust with clients and partners. In a digital world full of cyber risks, ISO 27001 shows you’re serious about information security.
Yes, absolutely. Many clients—especially in regulated industries—prefer or even require their vendors to be ISO 27001 certified. It gives you a competitive edge by proving your organization meets globally accepted information security standards. It’s often a key factor in securing partnerships and long-term business relationships.
Beyond compliance, ISO 27001 helps identify inefficiencies, reduce redundant processes, and improve communication around security. It encourages a culture of risk awareness across departments and provides a clear roadmap for managing threats, which ultimately saves time, money, and potential damage to your reputation.
While ISO 27001 is not a legal requirement in most cases, it helps your organization comply with many privacy and security regulations like GDPR, HIPAA, or DORA. Many industries adopt ISO 27001 to align with legal expectations and demonstrate due diligence in protecting sensitive data.
Emerging trends in governance risk and compliance solutions include AI-driven risk assessments, automation of compliance processes, and cloud-based GRC platforms. Enterprises are adopting integrated risk management (IRM) approaches to enhance security, efficiency, and compliance readiness.
